
In the two previous blog entries on personal independence inspection process, I addressed the organizational drivers of cost efficiency and localization. While there is more to say on the organizational benefits, what about the privacy of the user data being inspected? Data privacy is one of the most discussed topics in the business community today. The data that is provided in an inspection is personal and confidential – tax filing and brokerage statements must be treated with due care.
While there is more to say on the organizational benefits, what about the privacy of the user data being inspected? Data privacy is one of the most discussed topics in the business community today. The data that is provided in an inspection is personal and confidential – tax filing and brokerage statements must be treated with due care.
First, let us study the current process to determine whether it handles data privacy well.
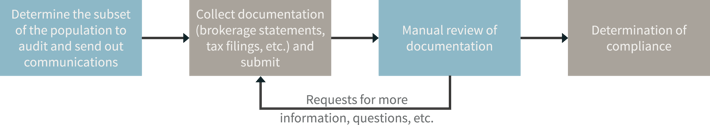
Today, the most common communication vehicle is email. An email is sent to begin the process, and then users send back information as attachments in emails. Most emails are not encrypted in transit nor are there controls in place to prevent information from being transferred to other individuals (onward transfer). As there are questions about the information sent in email, further emails are exchanged – likely disclosing some level of personal and confidential information as plain text. Next, any number of individuals are reviewing the document in a non-auditable fashion. The lack of controls are pervasive throughout the process.
Our viewpoint is that by enabling the process through technology, you are able to experience much better control of the privacy and confidentiality of your data. The control is established in the following ways:
Encryption: As all data exchange is in the application, the data is secure in transit through secure web traffic – similar to purchasing an item on Amazon.com. Second, data may be encrypted in the database (encryption at rest). Through these encryption mechanisms, the data is secure from prying eyes at all times.
Auditability: Every notification is sent out of the application, meaning we now know who sent what message and when they sent it. By doing so, a full audit trail can be established, which is useful for monitoring the process and in the event that any disciplinary actions are necessary for those being inspected.
Surveillance: Every time an administrative user takes action or views a document, this information is logged. Gone are the days where it is unknown who is reviewing the data and when they may be passing it to others.
Redaction: Certain information that is contained in a document (e.g. brokerage statement) is unnecessary for the inspection process. What if the user could use a “black pen” on screen and remove the information from being stored? By putting control in the hands of the user, the user can make a determination, within policy bounds, of what to disclose through the process. Unlike paper documents that can be reconstructed, technology exists to have a secure removal of the information.
Information Retention: The information related to the inspection process may not be necessary after the inspection for the firm to keep. In accordance with your retention policies, the system can securely remove (e.g. wipe) the information so that it cannot be reconstructed. Unlike a paper shredder that may or may not be used and the user would never know the outcome, the system can provide a positive affirmation to the user of what data is being retained and what information has been destroyed.
In summary, our viewpoint is that the systematic approach is superior to the manual approach that exists today. In the next blog, let us examine how this approach improves the user experience.
These Stories on Enterprise Data Management


No Comments Yet
Let us know what you think